Ransomware is one of the most significant threats facing organisations today. Battling it is no easy task, particularly given that threat actors are continually refining their techniques and approaches. Recent shifts, for example, include tweaks to ransomware-as-a-service (RaaS) models; the adoption of new programming languages; evolutions in targeting and deployment; and increasingly launching attacks after business hours and at weekends to hinder detection and incident response efforts.
Written by
Organisations today confront a substantial menace in the form of ransomware, representing one of the most formidable challenges. Combatting this threat is a complex endeavour, especially considering that malicious actors are consistently enhancing their methodologies. Recent developments encompass adjustments to ransomware-as-a-service (RaaS) models, the integration of novel programming languages, shifts in targeting and deployment strategies, and a growing trend of executing attacks beyond regular business hours and during weekends to impede detection and incident response initiatives.
A notable trend in recent developments is the surge in remote ransomware incidents, where an organisation’s domain architecture is exploited to encrypt data on managed domain-joined machines. All malicious activities, including ingress, payload execution, and encryption, take place on an unmanaged machine, effectively bypassing modern security measures.
The only discernible sign of compromise lies in the transmission of documents to and from other machines. According to Sophos telemetry, intentional remote encryption attacks have seen a significant 62% year-on-year increase since 2022. Microsoft’s 2023 Digital Defense Report further reveals that approximately 60% of human-operated ransomware attacks involve remote encryption, with 80% of compromises originating from unmanaged devices, underscoring a deficiency in active asset management. Ransomware families supporting remote encryption include Akira, ALPHV/BlackCat, BlackMatter, LockBit, and Royal. This technique has been in use for some time; CryptoLocker, dating back to 2013, was already targeting network shares.
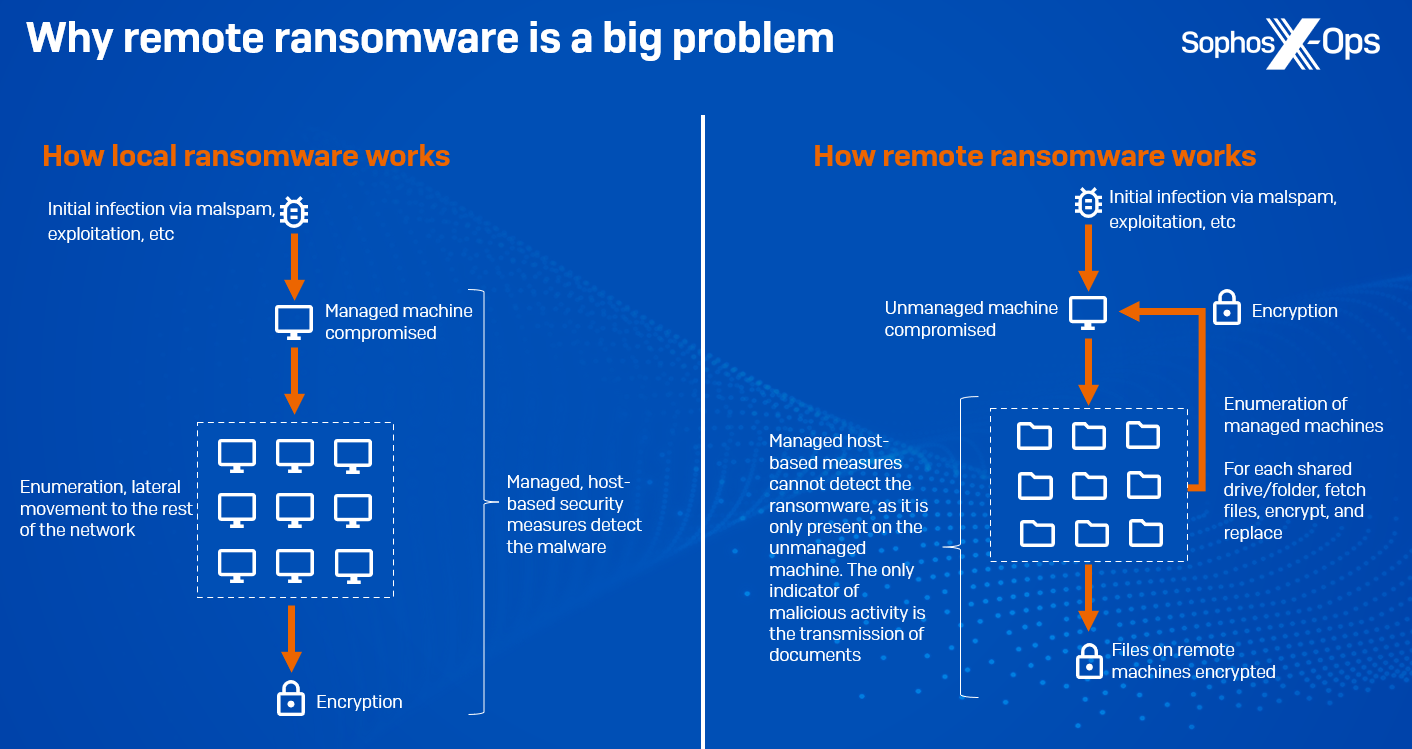
Figure 1: A simplified explanation of how remote ransomware works
Not surprisingly, the surge and ongoing evolution of ransomware have prompted extensive research focused on its detection and prevention. Academics, security researchers, and vendors are actively putting forth diverse solutions to address this malware threat. Ransomware, being a distinctive form of malware, poses specific practical and intellectual challenges, and the diversity of solutions mirrors this complexity. Many of these solutions aim at countering one or more of ransomware’s unique behavioral characteristics, such as filesystem enumeration, file access and encryption, and ransom note generation. Meanwhile, some solutions take a more generic approach, applying common anti-malware techniques to combat ransomware.
In the second instalment of our new technical thought leadership series (the first, focusing on memory scanning, can be found here), we will offer a brief overview of various techniques along with their respective advantages and disadvantages. Subsequently, we will delve into an in-depth examination of our own contribution to the field: CryptoGuard.
Before delving into the specifics, it’s important to acknowledge that a ransomware attack unfolds through multiple stages, with the majority occurring before the solutions discussed in this article become relevant. A well-protected enterprise typically employs multiple layers of defense, deterring attacks at various junctures. This often renders specific anti-ransomware solutions unnecessary. However, in instances where all preventive measures fail and a determined adversary reaches the encryption stage, we require technology capable of preventing irreversible damage. While other phases of an attack, such as initial infection, persistence, lateral movement, and so forth, are reversible, encryption stands out as an irreversible stage.
Anti-ransomware methods
Static Solutions
Static techniques, referring to methods that can be carried out passively without executing the malware, for detecting ransomware do not significantly differ from those employed to detect other types of malware. Solutions within this category encompass signature-matching, string comparison, file operation comparison, analysis of behavioural traits, deep learning techniques, and examination of PE headers.
Although static methods offer the advantage of being relatively quick and cost-effective, determined attackers can circumvent them by altering code until signature detections are compromised. Moreover, these methods exhibit lower efficacy against novel variants, packers, Obfuscators, in-memory threats, and remote ransomware.
Dynamic Solutions
Dynamic solutions, on the other hand, tend to be more computationally expensive, but offer greater coverage. Dynamic anti-ransomware solutions in this vein include the following:
Filesystem interactions
Certain security solutions keep a vigilant eye on alterations to file extensions, frequent read/write and renaming activities, or the creation of new files associated with ransomware variants. Conversely, alternative solutions rely on different approaches. Take the open-source project Raccine, for instance, which operates on the principle that numerous ransomware variants eliminate shadow copies through vssadmin. Raccine functions by intercepting requests to vssadmin and terminating the responsible process.
Given that ransomware specifically targets files, it appears reasonable that various strategies should center around filesystem interactions. However, a considerable number of these strategies depend on analysis within a sandboxed environment, are based on identifying abnormal patterns that threat actors might intentionally avoid generating, or can be resource-intensive due to the extensive monitoring required (although it is feasible to dynamically adjust the monitoring intensity). Additionally, certain filesystem-based techniques may prove ineffective in countering remote ransomware
Folder shielding
Although tools like Controlled Folder Access (CAF) within Windows Defender restrict folder access to specific applications, this strategy is primarily designed for individual users. CAF enhances ransomware protection by limiting unauthorised access to specified folders, permitting only trusted applications to make changes to files within those folders. However, in the context of business networks, this approach may prove less practical due to the continuous demand for detailed management of folders and applications. Moreover, it does not mitigate the risk of attacks gaining control over trusted applications, a common tactic employed in ransomware attacks.
API calls
Certain security solutions analyse API calls initiated by a process, either by flagging uncommon and suspicious calls or by identifying potentially malicious call sequences.
The majority of ransomware utilises API calls, although certain variants employ evasive tactics to conceal them, especially for API calls recognised as suspicious, such as CreateRemoteThread or VirtualAllocEx, commonly associated with process injection, or API calls related to encryption. Monitoring API calls at the kernel level appears to be a valuable strategy, but this monitoring is resource-intensive, prone to generating false positives, and challenging to implement on a large scale. Additionally, in the case of remote ransomware, the process itself may not reside on the host under attack, posing a challenge to this approach
Honeyfiles
Numerous security products utilise terms like ‘honeyfiles,’ ‘decoy files,’ ‘bait files,’ or ‘canary files’ as a countermeasure against ransomware. These inconspicuous files are positioned in a directory, and genuine users are advised not to interact with them. A dedicated monitoring system, either at the user or kernel level, activates if any process accesses or modifies these files, triggering an alert.
Honeyfiles offer a lightweight and low-effort solution, serving as an early warning mechanism for potential attacks. However, they come with certain considerations. Defenders must ensure that alerts are received and acted upon promptly, given that an attack is already underway when a honeyfile is triggered. Additionally, strategic placement is crucial—deep enough within file systems to avoid accidental triggering by regular users and processes, yet not so deep that critical documents get encrypted before being accessed.
Fingerprinting
A less conventional method involves ‘fingerprinting’ specific malicious patterns, whether in network (C2) traffic, CPU consumption, or CPU signals.
In the context of network traffic, it’s crucial to highlight that in contemporary human-led ransomware attacks, threat actors customise and compile the ransomware binary uniquely for each victim. This strategic approach aims to hinder detection and complicate the decryption process. The tailor-made ransomware typically includes a victim-specific ransom note and is deployed in a ‘fire-and-forget’ manner, eliminating the necessity for direct communication with the threat actor. The encryption process is self-contained within the malware, utilizing a victim-specific embedded public key.
Intel introduces an emerging technology called Threat Detection Technology (TDT), offering hardware-level ransomware detection. SE Labs’ review showcases remarkable effectiveness against a variety of encryption schemes. However, this technology is confined to specific Intel CPUs, excluding ARM and AMD architectures. This limitation arises from TDT relying on a machine learning model trained on CPU performance signals from specific ransomware families’ encryption profiles. The model, trained by Intel, depends on vendor support and does not function with remote encryption. A drawback of this technology is that certain ransomware strains, like LockBit and Akira, intentionally encrypt only a portion of each file, accelerating the attack’s impact and compromising a substantial number of files before detection by Intel TDT occurs.
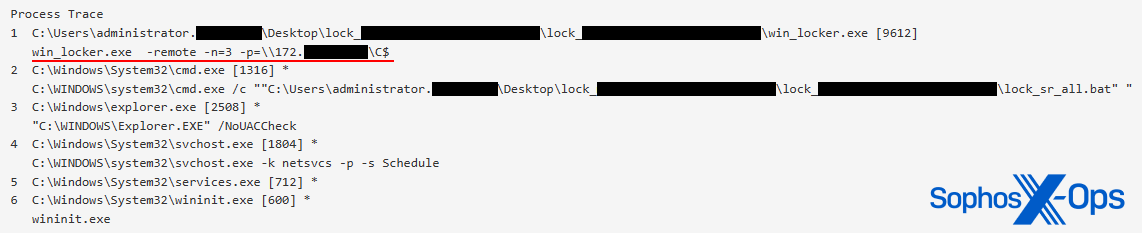
Figure 2: Akira ransomware, specifically attacking only remote data, and encrypting only 3% of each file
Automated telemetry-driven containment
Contemporary endpoint protection solutions often send data to the cloud for incident response and alert analysis. Nevertheless, the automatic reconstruction of the intricacies of an ongoing human-led ransomware attack based on alert telemetry can vary significantly, ranging from a few minutes to several hours. This delay is influenced by factors such as the set telemetry reporting frequency, the existence of additional alert signals, and the cloud’s processing capability to compile and correlate specific events from various protected machines.
After detection, an automated response may involve implementing a containment policy on managed devices to isolate a specific user account suspected of compromise by an attacker. This action is intended to thwart an imminent or ongoing (remote) ransomware encryption attack stemming from the identified account. However, it’s crucial to recognise that disseminating this policy also takes time, potentially up to several hours. Additionally, in cases where the attacker initiates encryption without triggering prior alerts on managed machines (considering the aforementioned statistic that 80% of attacks involve unmanaged machines) or chooses to commence the encryption process from an alternative user account, the conditions may not always align for an effective cloud-driven dynamic containment strategy. Nonetheless, it can prove beneficial in certain scenarios.
Rollback
Typically, dynamic anti-ransomware solutions often require some level of encryption or data manipulation to occur before detecting the attack. Consequently, a certain number of files are likely to undergo encryption, necessitating the use of a backup and restore function to recover affected files.
To restore unencrypted file versions, certain endpoint protection products utilise Volume Shadow Copies, a Windows feature that creates data snapshots at specific time intervals. These ‘shadow copies’ capture file or volume states, even while they are in use. However, this approach has its limitations: attackers often delete the shadow copies, it does not safeguard files on network mapped drives, and successful rollback depends on detecting and addressing the ransomware incident before the subsequent scheduled snapshot (typically occurring every four hours). Since most attacks happen after office hours, this method can complicate recovery efforts.
Contact the team today to learn more about how to approach your ransomware battle.
